Verifying installer signatures
Bitvise software installers are cryptographically signed. Our most recent installers use an Extended Validation digital certificate from DigiCert. Do not run installers for Bitvise software that do not carry a valid digital signature by Bitvise.
To verify a digital signature for any downloaded Windows executable:
Before starting the executable, use Windows File Explorer to open the folder where it resides.
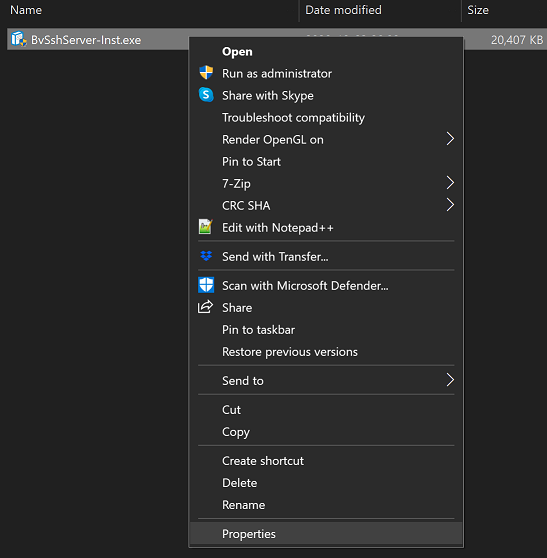
Right-click the executable for the context menu. Select Properties.
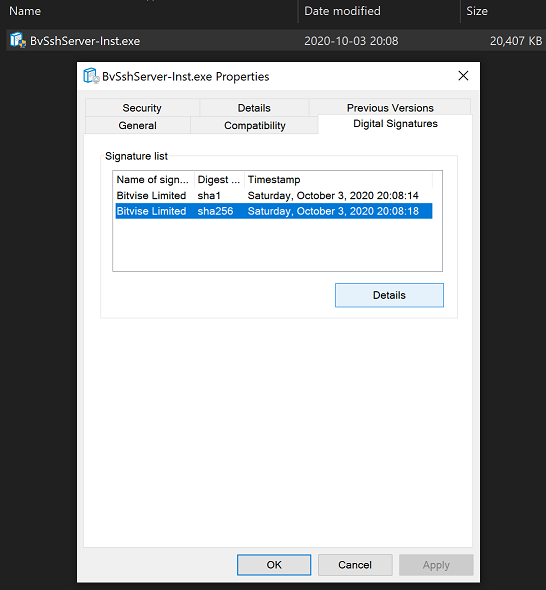
Verify that the Properties dialog shows a Digital Signatures tab. Open it.
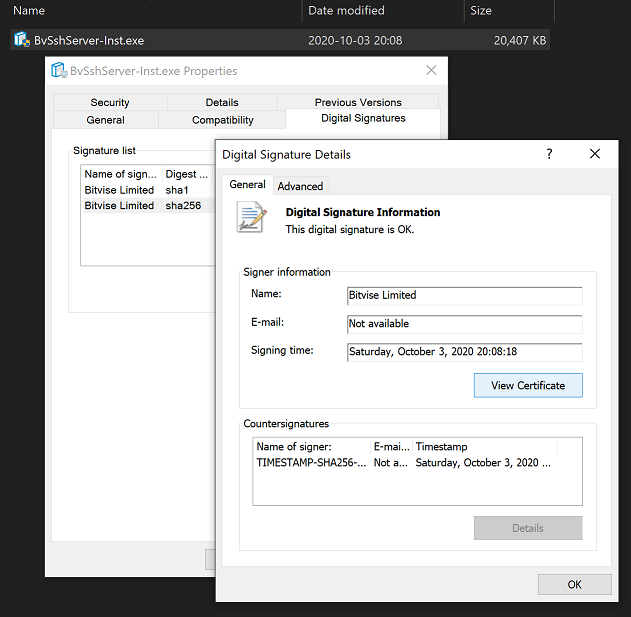
Select a signature and click Details. Verify that the window says: "This digital signature is OK."
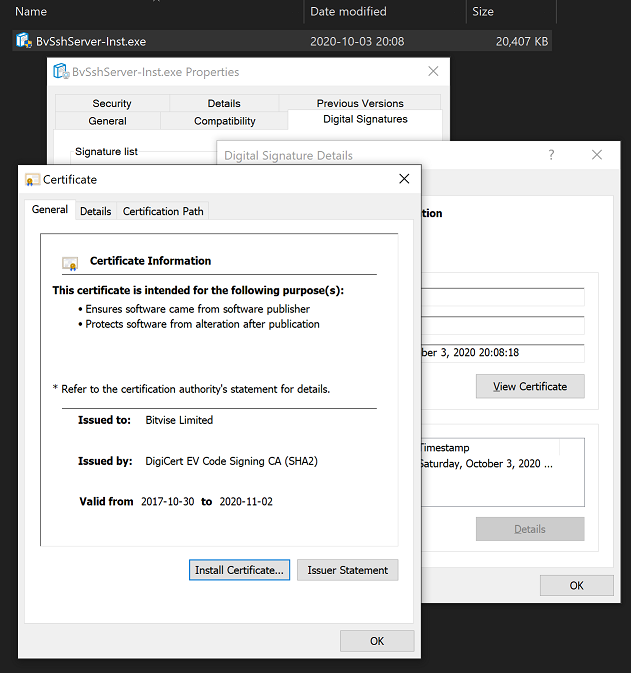
If you like, click View Certificate to see further certificate details.
See below screenshots.
Q. Why not just verify the installer by checking a hash?
If we publish cryptographic digests of installers on our website, this provides no additional security beyond a secure download link.
Our downloads and our website are already secured using HTTPS. When you verify a plain hash, you are checking something you received secured by TLS, against something else you received also secured by TLS. There is very marginal additional security.
A digital signature provides additional security. The private key used for TLS is kept online and is frequently used. But the private key used for code signing is kept offline and is rarely used. The chain of custody for the key is separate. Your chain of trust for the certificate is also separate. The validation processes for code signing certificates are more stringent. This provides significant additional assurance that the executable you run is authentic.